Until we will have intelligent buildings, which will be able to give commands by voice, control over the work of all devices installed in the building will be supported by the Integrated Management System.
One computer is enough to efficiently manage the devices used for day-to-day operation or security. The Integrated Management System allows you to work both automatically and with the operator. In the first option, decisions are made strictly according to programmed algorithms. In the case of working with an operator, the software also watches over the whole time, proposing specific solutions, which is useful in the case of emergencies, alarm situations and helps the person controlling the network to avoid making a mistake. All events taking place in the facility are immediately captured by the Integrated Management System, making it possible to react immediately.
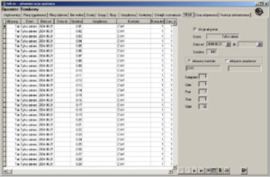
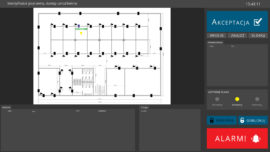
a) work with the operator is carried out only on the basis of plans for facilities graphically presented on a monitor in the form of maps (buildings, storeys, fragments of the facility).
b) Each of the controlled devices is graphically presented on the map in the form of a (thematic) icon, showing the currently performed task (opening the door, turning on the light, etc.)
c) all actions of the subsystem are immediately interpreted graphically on the monitor, and Actions requiring confirmation are displayed with an additional request for acceptance by the operator.
d) Each alarm event is immediately signaled by an alarm message, an appropriate voice message and a request to confirm the receipt of the message by the operator.
e) Remote management of the Integrated Management System actions (opening the door, turning on the camera view, air conditioning, etc.) consists in pointing the mouse cursor on the appropriate icon on the map of interest to us and "clicking" within the icon. In the case of an action requiring confirmation, an appropriate message is displayed along with a confirmation request.
f) If the Integrated Management System is combined with the sound system in the facility, each message, both alarm and information, can be transmitted to any zone in the facility.
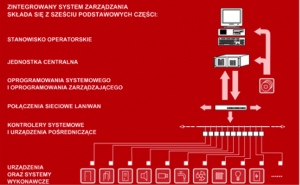
The key advantage of the Integrated Management System is its great flexibility. The possibilities of its expansion are practically unlimited and depend only on the needs and requirements of the user, and the decision-making process in each case takes the same time. Therefore, there is no risk that in the case of a big network, the reaction of the software will take too long. The architecture diagram is presented below:
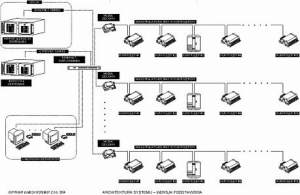
The Integrated Management System has been designed to perform three basic tasks:
- Integrated monitoring of local programs and devices in order to visualize all events taking place in the facility. In the event that various local systems (alarm, fire, panic, ventilation, access control etc.) operate independently on the site, the control consisting in supervising and analyzing their work may be time consuming, not to mention the lack of information exchange. between them. Integrated monitoring is based on the constant gathering of data on the current operation of all installations and displaying them on the screens of the appropriate monitors. This gives the operator a detailed view of all the most important parameters and enables quick reaction in situations where it is required. Part of the operator's activities is taken over by the computer system and performed automatically.
- Managing and supervising the operation of local devices and installations in an automatic manner with full control by the system operator. No operator intervention is required for the daily operation of many devices. It can be carried out in a fully automatic manner, after prior set up of the scheme according to which the devices will work, and any possible changes to it are very simple and quick to be performed by trained personnel without the need for specialist service. Of course, the operator can take control of the Integrated Management System at any time.
- Managing the operation of individual devices directly by the operator (or operators) from the command point. It is a work pattern that requires an appropriate number of operators capable of making specific decisions, however, it causes that each decision is made by a person with appropriate competences. Of course, each of his decisions is irreversibly saved in the database with his personal identifier and exact (to the second) time. In addition, some of his decisions require (apart from the presence of a personal identifier in the form of an RF card in the reader) to provide an access password (double control on the principle: "I have something and I know something"). In the event that any of the operators of the Integrated Management System is at risk, and thus there is a risk of unauthorized control of the software, it is possible to block the operator's work by logging out remotely (from another operator terminal) and withdrawing his rights to operate the system.

The Integrated Management System allows you to connect both workstations that allow you to view and control the program on the operator's monitor, as well as to visualize its behavior (for presentation purposes only). The network has been designed in such a way as to enable connection of an unlimited number of workstations, both for network operators and presentation operators. As a standard, the operator stations are secured with a controller that checks the validity of the user ID on an ongoing basis. Any actions can be taken only when the identifier is placed in the controller and the rights granted to the operator allow their execution. With the required increased level of security, the operator panel can be additionally protected with an operator password. Each registered operator has individual access rights, e.g. to the entire facility or part of it (building, floor) and may at any time perform an analysis of the state of each of the devices and subsystems under his control.
-

AC-AT02 Proximity terminal
Read more -

AC-CPU100 Central Unit
Read more -

AC-PP1P1S Button panel
Read more -

Admin module AC-S025/ADM
Read more -

Bolt controller EB-LCM11A
Read more -

Bolt Controller EB-LCM21A
Read more -

Controller EB-BC244A
Read more -

EB-AC2201 Controller
Read more -

EB-BC280A Controller
Read more -

EB-BC280A Controller
Read more -

EB-MTR5 network module
Read more -

Operator module AC-S025/OPR
Read more